Understanding Linux file permissions is crucial for effective system administration in Linux. In this guide, we’ll delve into the intricacies of setting file permissions, covering definitions, command syntax, and practical examples to empower you in managing access rights effectively. #centlinux #linux #ubuntu
Table of Contents
1. Understanding Linux File Permissions
Linux File permissions determine who can access, modify, or execute files. There are three types of permissions:
- Read (r): Allows the file to be viewed and its contents read.
- Write (w): Permits the modification, addition, or deletion of a file’s content.
- Execute (x): Enables the execution of scripts or binary files.

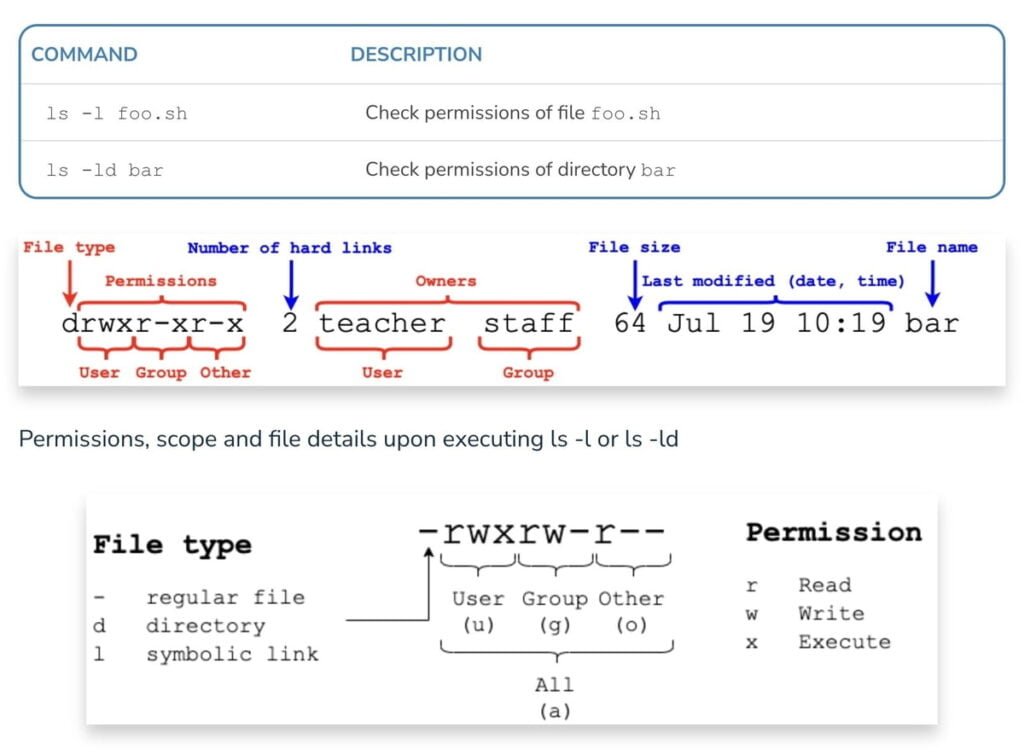
2. How to check permissions of a File in Linux?
You can view current permissions using the ‘ls’ command with the ‘-l’ option:
// View Permissions
$ ls -l3. How do you change File Permissions in Linux?
To modify permissions, you’ll use the ‘chmod’ command. Below is an example of granting read and write permissions to a file:
// Granting Read and Write Permissions
$ chmod +rw filename4. Using Numeric Permissions
Numeric permissions provide a concise way to set permissions. Each permission type is assigned a value:
- Read (4): 4
- Write (2): 2
- Execute (1): 1
For example, to give read, write, and execute permissions, you’d use:
// Setting Read, Write, and Execute Permissions
$ chmod 7xx filename5. Changing Ownership with chown command
The ‘chown’ command allows you to change the owner of a file. Below is an example of changing ownership to a specific user:
// Changing Ownership
$ sudo chown username filename6. Modifying Group Ownership with chgrp command
‘chgrp’ is used to change the group ownership of a file. Here’s an example:
// Changing Group Ownership
$ sudo chgrp groupname filename7. Setting Default Permissions with umask command
The ‘umask’ command sets default permissions for newly created files. To, for instance, deny write permissions for group and others, you’d use:
// Setting Default Permissions
$ umask 0228. Special Permissions
In addition to basic permissions, Linux has special permissions:
- SUID: Allows a user to execute a file with the permissions of the file owner.
- SGID: Enables a user to execute a file with the permissions of the group owner.
- Sticky Bit: Restricts file deletion to the file owner, even if others have write permissions.
Special permissions in Linux enhance security and functionality beyond basic Linux file permissions. This comprehensive guide explores the definitions, command syntax, and practical examples of special permissions. By the end, you’ll have a deep understanding of how to utilize these features effectively in your Linux system.
a. Set User ID (SUID)
The SUID permission allows a user to execute a file with the permissions of the file owner. It is represented by ‘s’ in the owner’s execute field.
// Setting SUID
$ chmod u+s filenameb. Set Group ID (SGID)
The SGID permission allows a user to execute a file with the permissions of the group owner. It is represented by ‘s’ in the group’s execute field.
// Setting SGID
$ chmod g+s directoryc. Sticky Bit
The Sticky Bit ensures only the file owner can delete or rename their files within a directory, even if others have write permissions. It is represented by ‘t’ in the directory’s execute field.
// Setting Sticky Bit
$ chmod +t directoryd. Removing Special Permissions
To remove special permissions, use the ‘chmod’ command with the corresponding prefix:
// Removing SUID
$ chmod u-s filename
// Removing SGID
$ chmod g-s directory
// Removing Sticky Bit
$ chmod -t directorye. Practical Applications
Special permissions are valuable in scenarios like:
- Setting up privileged utilities: Ensuring specific tasks can be executed with elevated Linux file permissions.
- Multi-user collaboration: Facilitating secure file sharing within groups.
- Temp directories: Allowing users to create and manage temporary files securely.
f. Linux File Permission Cheat Sheet
If you’re serious about leveling up your Linux skills, I highly recommend the Linux Mastery: Master the Linux Command Line in 11.5 Hours by Ziyad Yehia course. It’s a practical, beginner-friendly program that takes you from the basics to advanced command line usage with clear explanations and hands-on exercises. Whether you’re a student, sysadmin, or developer, this course will help you build the confidence to navigate Linux like a pro.
👉 Enroll now through my affiliate link and start mastering the Linux command line today!
Disclaimer: This post contains affiliate links. If you purchase through these links, I may earn a small commission at no extra cost to you, which helps support this blog.
Final Thoughts
Mastering Linux file permissions is pivotal for secure and efficient system management. By understanding the concepts and commands outlined in this guide, you’ll be well-equipped to control access rights and maintain the integrity of your files and directories.
Struggling with Linux server management? I offer professional support to ensure your servers are secure, optimized, and always available. Visit my Freelancer profile to learn more!
Frequently Asked Questions (FAQs)
Q1: What does the sticky bit do in Linux file permissions?
The sticky bit prevents users from deleting or renaming files in a shared directory unless they own the file, enhancing security in shared folders like /tmp.
Q2: Can Linux file permissions control users in the same group differently?
No, file permissions apply the same way to all users in a group. To differentiate users in the same group, Access Control Lists (ACLs) are needed.
Q3: What happens if a file has no execute permission for its owner?
The owner cannot run the file as a program or script, but can still read or write it depending on other permissions.
Q4: How do symbolic links affect file permissions?
Permissions on a symbolic link don’t matter; access depends on the permissions of the target file or directory it points to.
Q5: Why would a directory need execute permission?
Execute permission on a directory lets you “enter” it or access its contents, even if you have read permission to list files. Without execute, you can’t open files inside.

Leave a Reply
You must be logged in to post a comment.