Discover how to Chroot Jail Apache in Linux with our comprehensive guide. Enhance your web server security by isolating Apache processes from the rest of the system. #centlinux #linux #apache
Table of Contents
What is Chroot Jail?
In Linux, Chroot is an operation to change the apparent root directory i.e. / for a running process and their child processes. The process running in Chroot can not access the files and commands outside that environmental directory tree. This modified environment is called a Chroot Jail.
A chroot environment is relatively difficult to set up than a traditional install, especially if we run other software like MySQL, PHP, Python, etc.

Why to Chroot Jail Apache?
By chrooting the Apache web server, we do not actually increase the security, rather we limit the access to files and commands by the httpd process and decreases the possible impact, when an Apache web server is compromised. Also potentially dangerous CGI scripts can only access the environmental root directory.
In this post, we will set up a chroot jail Apache Web Server in Linux, and create the systemd unit to auto-start the httpd service.
Recommended Training: Apache Web Server from Vipin Gupta

System Specification
We are using a Linux machine with following specification for this demonstration.
- Hostname – webserver-01.example.com
- IP Address – 192.168.116.61/24
- Operating System – RHEL 7.5
TP-Link AX1800 WiFi 6 Router V4 (Archer AX21) – Dual Band Wireless Internet, Gigabit, Easy Mesh, Works with Alexa – A Certified for Humans Device, Free Expert Support
$54.99 (as of July 4, 2025 20:44 GMT +00:00 – More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Chroot Jail Apache Web Server
Connect to our Linux machine using ssh and create the directory for setting up the chroot jail.
mkdir -p /chroot/httpd/We have already configured the local yum repository on the machine. Please refer to my previous article Configure Local Yum Repository using ISO in Linux.
Now, we are installing Apache web server using yum, but in a non-default directory.
yum install -y httpd --installroot=/chroot/httpdAbove command will install the Apache Web Server and its dependencies in the /chroot/httpd. You may observe that, it installs many packages that were already installed on the default root /. These packages are reinstalled in /chroot/httpd for the sake of chroot jail setup.
Create some required devices for the chroot environment.
cd /chroot/httpd/dev
rm -f null
mknod /chroot/httpd/dev/null c 1 3
mknod /chroot/httpd/dev/random c 1 8
mknod /chroot/httpd/dev/urandom c 1 9
ls -alOutput:
total 0
drwxr-xr-x. 2 root root 47 Sep 2 19:26 .
dr-xr-xr-x. 17 root root 224 Sep 2 19:17 ..
crw-r--r--. 1 root root 1, 3 Sep 2 19:26 null
crw-r--r--. 1 root root 1, 8 Sep 2 19:26 random
crw-r--r--. 1 root root 1, 9 Sep 2 19:26 urandom
Add a default homepage for Apache web server.
cd /chroot/httpd/var/www/html/
cat >> index.html << EOF
<html>
<head><title>Test Page</title></head>
<body><h1>Apache Homepage from Chroot Jail.</h1></body>
</html>
EOFAllow httpd service to communicate through Firewall.
firewall-cmd --permanent --add-service=http
firewall-cmd --reloadConfigure systemd unit to autostart httpd service. First copy the required configuration files from chroot jail to host environment.
cp /chroot/httpd/etc/sysconfig/httpd /etc/sysconfig/
cp /chroot/httpd/usr/lib/systemd/system/httpd.service /usr/lib/systemd/system/Now edit the httpd.service unit to start Apache in chrooted environment.
vi /usr/lib/systemd/system/httpd.serviceSearch and update the following three lines.
Type=simple
ExecStart=/sbin/chroot /chroot/httpd /usr/sbin/httpd $OPTIONS -DFOREGROUND
ExecReload=/sbin/chroot /chroot/httpd /usr/sbin/httpd $OPTIONS -k gracefulFor further clarification, the differences in files after editing are shown below.
diff /chroot/httpd/usr/lib/systemd/system/httpd.service /usr/lib/systemd/system/httpd.serviceOutput:
8c8
< Type=notify
---
> Type=simple
10,11c10,11
< ExecStart=/usr/sbin/httpd $OPTIONS -DFOREGROUND
< ExecReload=/usr/sbin/httpd $OPTIONS -k graceful
---
> ExecStart=/sbin/chroot /chroot/httpd /usr/sbin/httpd $OPTIONS -DFOREGROUND
> ExecReload=/sbin/chroot /chroot/httpd /usr/sbin/httpd $OPTIONS -k graceful
Start and enable httpd service.
systemctl daemon-reload
systemctl start httpd
systemctl enable httpdCheck root directory for running httpd service. First we obtain the PID of the httpd process and then check it’s root directory in the proc folder.
systemctl status httpdOutput:
â httpd.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; enabled; vendor preset: disabled)
Active: active (running) since Sun 2018-09-02 20:18:23 PKT; 1min 16s ago
Docs: man:httpd(8)
man:apachectl(8)
Main PID: 10620 (httpd)
CGroup: /system.slice/httpd.service
ââ10620 /usr/sbin/httpd -DFOREGROUND
ââ10639 /usr/sbin/httpd -DFOREGROUND
ââ10640 /usr/sbin/httpd -DFOREGROUND
ââ10641 /usr/sbin/httpd -DFOREGROUND
ââ10642 /usr/sbin/httpd -DFOREGROUND
ââ10643 /usr/sbin/httpd -DFOREGROUND
Sep 02 20:18:23 webserver-01.example.com systemd[1]: Started The Apache HTTP ...
Sep 02 20:18:23 webserver-01.example.com systemd[1]: Starting The Apache HTTP...
Hint: Some lines were ellipsized, use -l to show in full.
Now find the root directory of the process by PID.
ls /proc/10620/root -alOutput:
lrwxrwxrwx. 1 root root 0 Sep 2 20:20 /proc/10620/root -> /chroot/httpd
Browse the URL http://webserver-01.example.com/ from a client’s browser to verify the httpd service.
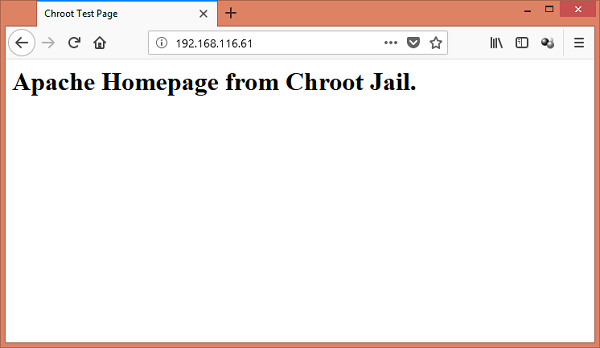
We have successfully set up a chroot jail for our Apache Web Server in Linux.
The Linux Memory Manager
$67.99 (as of July 4, 2025 20:44 GMT +00:00 – More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Final Thoughts
Implementing a Chroot Jail for Apache in Linux can greatly improve your web server’s security by isolating its processes from the rest of the system. By following this guide, you can ensure a more secure and robust environment for your web applications.
Struggling with AWS or Linux server issues? I specialize in configuration, troubleshooting, and security to keep your systems performing at their best. Check out my Fiverr profile for details.



Leave a Reply
You must be logged in to post a comment.