Learn how to install FreeIPA on CentOS 7 with this comprehensive guide. Step-by-step instructions, prerequisites, and tips to set up FreeIPA for centralized identity management and authentication on your Linux server. #centlinux #linux #freeipa
Table of Contents
What is FreeIPA Server?
FreeIPA server provides centralized authentication, authorization and account information by storing data about users, groups, hosts and other objects necessary to manage the security aspects of a network of computers.
FreeIPA is built on top of well-known open-source components and standard protocols with a very strong focus on ease of management and automation of installation and configuration tasks.
The 389 Directory Server is the main data store in FreeIPA and provides a full multi-master LDAPv3 directory infrastructure.
Single-Sign-on authentication is provided via the MIT Kerberos KDC (Key Distribution Center).
Authentication capabilities are augmented by an integrated Certificate Authority based on the Dogtag project.
Optionally Domain Names can be managed using the integrated ISC Bind server.
Security aspects related to access control, delegation of administration tasks and other network administration tasks can be fully centralized and managed via the Web UI or the ipa Command Line tool.
Following diagram will give a clear idea of the FreeIPA components and its interoperability.
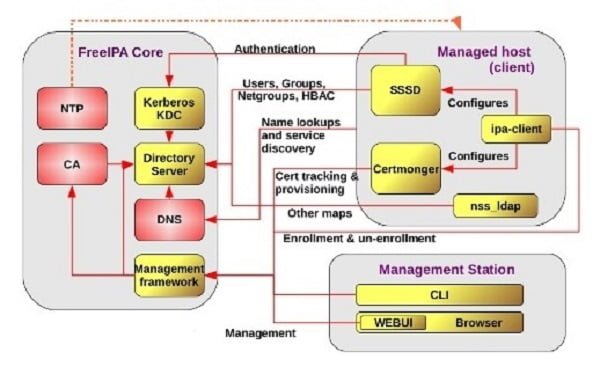
Here, configurations are performed through Linux CLI (Command Line Interface). Therefore, we strongly recommend you should attend following Training:
Recommended Training: The Linux Command Line Bootcamp: Beginner To Power User from Colt Steele

Linux Server Specification
We have a CentOS 7 virtual machine with following specifications.
- CPU – 2.4 Ghz (2 cores)
- Memory – 2 GB
- Storage – 20 GB
- Operating System – CentOS 7
- Hostname – ipaserver.example.com
- IP Address – 192.168.116.200/24
- Gateway – 192.168.116.2
- DNS Server – 192.168.116.2
Amazon Fire 7 Kids tablet (newest model) ages 3-7. Top-selling 7″ kids tablet on Amazon. Includes ad-free and exclusive content, easy parental controls, 10-hr battery, 16 GB, Purple
$54.99 (as of July 9, 2025 21:12 GMT +00:00 – More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Install FreeIPA on CentOS 7
FreeIPA Server is included with RHEL / CentOS 7 ISO. Therefore, you need a local yum repository to install it.
You can refer to our previous post to setup a local yum repository using RHEL 7 ISO and you can use it to install FreeIPA on CentOS 7 along with relevant packages.
yum install -y ipa-server bind-dyndb-ldap bindConfigure FreeIPA Server on CentOS 7
Now, configure the FreeIPA Server as follows.
ipa-server-install --setup-dnsOutput:
The log file for this installation can be found in /var/log/ipaserver-install.log
==============================================================================
This program will set up the IPA Server.
This includes:
* Configure a stand-alone CA (dogtag) for certificate management
* Configure the Network Time Daemon (ntpd)
* Create and configure an instance of Directory Server
* Create and configure a Kerberos Key Distribution Center (KDC)
* Configure Apache (httpd)
* Configure DNS (bind)
To accept the default shown in brackets, press the Enter key.
WARNING: conflicting time&date synchronization service 'chronyd' will be disabled
in favor of ntpd
Existing BIND configuration detected, overwrite? [no]: yes
Enter the fully qualified domain name of the computer
on which you're setting up server software. Using the form
.
Example: master.example.com.
Server host name [ipaserver.example.com]:
Warning: skipping DNS resolution of host ipaserver.example.com
The domain name has been determined based on the host name.
Please confirm the domain name [example.com]:
The kerberos protocol requires a Realm name to be defined.
This is typically the domain name converted to uppercase.
Please provide a realm name [EXAMPLE.COM]:
Certain directory server operations require an administrative user.
This user is referred to as the Directory Manager and has full access
to the Directory for system management tasks and will be added to the
instance of directory server created for IPA.
The password must be at least 8 characters long.
Directory Manager password:
Password (confirm):
The IPA server requires an administrative user, named 'admin'.
This user is a regular system account used for IPA server administration.
IPA admin password:
Password (confirm):
Do you want to configure DNS forwarders? [yes]:
Enter the IP address of DNS forwarder to use, or press Enter to finish.
Enter IP address for a DNS forwarder: 192.168.116.2
DNS forwarder 192.168.116.2 added
Enter IP address for a DNS forwarder:
Do you want to configure the reverse zone? [yes]:
Please specify the reverse zone name [116.168.192.in-addr.arpa.]:
Using reverse zone 116.168.192.in-addr.arpa.
The IPA Master Server will be configured with:
Hostname: ipaserver.example.com
IP address: 192.168.116.200
Domain name: example.com
Realm name: EXAMPLE.COM
BIND DNS server will be configured to serve IPA domain with:
Forwarders: 192.168.116.2
Reverse zone: 116.168.192.in-addr.arpa.
Continue to configure the system with these values? [no]: yes
The following operations may take some minutes to complete.
Please wait until the prompt is returned.
Configuring NTP daemon (ntpd)
[1/4]: stopping ntpd
[2/4]: writing configuration
[3/4]: configuring ntpd to start on boot
[4/4]: starting ntpd
Done configuring NTP daemon (ntpd).
Configuring directory server (dirsrv): Estimated time 1 minute
[1/38]: creating directory server user
[2/38]: creating directory server instance
[3/38]: adding default schema
[4/38]: enabling memberof plugin
[5/38]: enabling winsync plugin
[6/38]: configuring replication version plugin
[7/38]: enabling IPA enrollment plugin
[8/38]: enabling ldapi
[9/38]: configuring uniqueness plugin
[10/38]: configuring uuid plugin
[11/38]: configuring modrdn plugin
[12/38]: configuring DNS plugin
[13/38]: enabling entryUSN plugin
[14/38]: configuring lockout plugin
[15/38]: creating indices
[16/38]: enabling referential integrity plugin
[17/38]: configuring certmap.conf
[18/38]: configure autobind for root
[19/38]: configure new location for managed entries
[20/38]: configure dirsrv ccache
[21/38]: enable SASL mapping fallback
[22/38]: restarting directory server
[23/38]: adding default layout
[24/38]: adding delegation layout
[25/38]: creating container for managed entries
[26/38]: configuring user private groups
[27/38]: configuring netgroups from hostgroups
[28/38]: creating default Sudo bind user
[29/38]: creating default Auto Member layout
[30/38]: adding range check plugin
[31/38]: creating default HBAC rule allow_all
[32/38]: initializing group membership
[33/38]: adding master entry
[34/38]: configuring Posix uid/gid generation
[35/38]: adding replication acis
[36/38]: enabling compatibility plugin
[37/38]: tuning directory server
[38/38]: configuring directory to start on boot
Done configuring directory server (dirsrv).
Configuring certificate server (pki-tomcatd): Estimated time 3 minutes 30 seconds
[1/22]: creating certificate server user
[2/22]: configuring certificate server instance
[3/22]: stopping certificate server instance to update CS.cfg
[4/22]: disabling nonces
[5/22]: set up CRL publishing
[6/22]: starting certificate server instance
[7/22]: creating RA agent certificate database
[8/22]: importing CA chain to RA certificate database
[9/22]: fixing RA database permissions
[10/22]: setting up signing cert profile
[11/22]: set certificate subject base
[12/22]: enabling Subject Key Identifier
[13/22]: enabling CRL and OCSP extensions for certificates
[14/22]: setting audit signing renewal to 2 years
[15/22]: configuring certificate server to start on boot
[16/22]: restarting certificate server
[17/22]: requesting RA certificate from CA
[18/22]: issuing RA agent certificate
[19/22]: adding RA agent as a trusted user
[20/22]: configure certificate renewals
[21/22]: configure Server-Cert certificate renewal
[22/22]: Configure HTTP to proxy connections
Done configuring certificate server (pki-tomcatd).
Configuring Kerberos KDC (krb5kdc): Estimated time 30 seconds
[1/10]: adding sasl mappings to the directory
[2/10]: adding kerberos container to the directory
[3/10]: configuring KDC
[4/10]: initialize kerberos container
[5/10]: adding default ACIs
[6/10]: creating a keytab for the directory
[7/10]: creating a keytab for the machine
[8/10]: adding the password extension to the directory
[9/10]: starting the KDC
[10/10]: configuring KDC to start on boot
Done configuring Kerberos KDC (krb5kdc).
Configuring kadmin
[1/2]: starting kadmin
[2/2]: configuring kadmin to start on boot
Done configuring kadmin.
Configuring ipa_memcached
[1/2]: starting ipa_memcached
[2/2]: configuring ipa_memcached to start on boot
Done configuring ipa_memcached.
Configuring ipa-otpd
[1/2]: starting ipa-otpd
[2/2]: configuring ipa-otpd to start on boot
Done configuring ipa-otpd.
Configuring the web interface (httpd): Estimated time 1 minute
[1/14]: setting mod_nss port to 443
[2/14]: setting mod_nss password file
[3/14]: enabling mod_nss renegotiate
[4/14]: adding URL rewriting rules
[5/14]: configuring httpd
[6/14]: setting up ssl
[7/14]: setting up browser autoconfig
[8/14]: publish CA cert
[9/14]: creating a keytab for httpd
[10/14]: clean up any existing httpd ccache
[11/14]: configuring SELinux for httpd
[12/14]: configure httpd ccache
[13/14]: restarting httpd
[14/14]: configuring httpd to start on boot
Done configuring the web interface (httpd).
Applying LDAP updates
Restarting the directory server
Restarting the KDC
Restarting the certificate server
Configuring DNS (named)
[1/11]: adding DNS container
[2/11]: setting up our zone
[3/11]: setting up reverse zone
[4/11]: setting up our own record
[5/11]: setting up records for other masters
[6/11]: setting up CA record
[7/11]: setting up kerberos principal
[8/11]: setting up named.conf
[9/11]: restarting named
[10/11]: configuring named to start on boot
[11/11]: changing resolv.conf to point to ourselves
Done configuring DNS (named).
Global DNS configuration in LDAP server is empty
You can use 'dnsconfig-mod' command to set global DNS options that
would override settings in local named.conf files
Restarting the web server
==============================================================================
Setup complete
Next steps:
1. You must make sure these network ports are open:
TCP Ports:
* 80, 443: HTTP/HTTPS
* 389, 636: LDAP/LDAPS
* 88, 464: kerberos
* 53: bind
UDP Ports:
* 88, 464: kerberos
* 53: bind
* 123: ntp
2. You can now obtain a kerberos ticket using the command: 'kinit admin'
This ticket will allow you to use the IPA tools (e.g., ipa user-add)
and the web user interface.
Be sure to back up the CA certificate stored in /root/cacert.p12
This file is required to create replicas. The password for this
file is the Directory Manager password
Allow aforementioned services and ports through Linux Firewall.
firewall-cmd --permanent --add-service={http,https,ldap,ldaps,dns,kerberos,ntp}
firewall-cmd --reloadFFJ Wireless Gaming Mouse, 24000 DPI, Tri-Mode 2.4G/USB-C/Bluetooth 5.3 Gaming Mouse Wireless, RGB Programmable Mouse Gamer, 75Hrs Battery Life, Rechargeable Gaming Mice for PC, Mac, PS5, Xbox – Black
$19.99 (as of July 9, 2025 20:21 GMT +00:00 – More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Install FTP Server on Linux
You have to make the CA certificate publicly available, so network clients can download and install it. Therefore, install an Anonymous FTP Server on your Linux operating system.
yum install -y vsftpdStart and enable vsftpd service.
systemctl enable vsftpd
systemctl start vsftpdAllow vsftpd service in Linux firewall.
firewall-cmd --permanent --add-service=ftp
firewall-cmd --reloadCopy the CA certificate to the FTP public folder to share it with network clients.
cp /root/cacert.p12 /var/ftp/pubCreate User on FreeIPA Server
To add a user we have to obtain a Kerberos ticket first.
kinit admin
klistOutput:
Ticket cache: KEYRING:persistent:0:0
Default principal: admin@EXAMPLE.COM
Valid starting Expires Service principal
07/27/2018 10:51:35 07/28/2018 10:51:32 krbtgt/EXAMPLE.COM@EXAMPLE.COM
You have obtain a Kerberos ticket. You can now run ipa commands.
Set default command shell for users.
ipa config-mod --defaultshell=/bin/bashOutput:
Maximum username length: 32
Home directory base: /home
Default shell: /bin/bash
Default users group: ipausers
Default e-mail domain: example.com
Search time limit: 2
Search size limit: 100
User search fields: uid,givenname,sn,telephonenumber,ou,title
Group search fields: cn,description
Enable migration mode: FALSE
Certificate Subject base: O=EXAMPLE.COM
Password Expiration Notification (days): 4
Password plugin features: AllowNThash
SELinux user map order: guest_u:s0$xguest_u:s0$user_u:s0$staff_u:s0-s0:c0.c1023$unconfined_u:s0-s0:c0.c1023
Default SELinux user: unconfined_u:s0-s0:c0.c1023
Default PAC types: MS-PAC, nfs:NONE
Create a user on our FreeIPA Server.
ipa user-add ahmer --first=ahmer --last=mehmood --passwordOutput:
------------------
Added user "ahmer"
------------------
User login: ahmer
First name: ahmer
Last name: mehmood
Full name: ahmer mehmood
Display name: ahmer mehmood
Initials: am
Home directory: /home/ahmer
GECOS: ahmer mehmood
Login shell: /bin/bash
Kerberos principal: ahmer@EXAMPLE.COM
Email address: ahmer@example.com
UID: 1692200001
GID: 1692200001
Password: True
Member of groups: ipausers
Kerberos keys available: True
Configuring DNS Server on CentOS 7
FreeIPA uses BIND to provide DNS services. Therefore, you can setup a DNS server for your network as follows.
ipa dnszone-mod --allow-transfer=192.168.116.0/24 example.comOutput:
Zone name: example.com
Authoritative nameserver: ipaserver.example.com.
Administrator e-mail address: hostmaster.example.com.
SOA serial: 1532711522
SOA refresh: 3600
SOA retry: 900
SOA expire: 1209600
SOA minimum: 3600
Active zone: TRUE
Allow query: any;
Allow transfer: 192.168.116.0/24;
Add MX record of the ipaserver.example.com in DNS Server.
ipa dnsrecord-add example.com @ --mx-rec="0 ipaserver.example.com."Output:
Record name: @
MX record: 0 ipaserver.example.com.
NS record: ipaserver.example.com.
Add an A record in DNS Server.
ipa dnsrecord-add example.com ipaserver --ttl=3600 --a-ip-address=192.168.116.200Output:
Record name: ipaserver
Time to live: 3600
A record: 192.168.116.200
SSHFP record: 1 1 C98798DE70AAF8F555A7C1EC4713A7B0F01F9905, 1 2 25B1928F52075F38A06C67EB8E3DD72D65C4EACF2F7A57F1912DCA83
CD486236, 3 1 5BAEFD0566A4CBEF40C24EC4EAD44371E96BE93B, 3 2
F4A6AAED25D658329C6B5AA865B99B4B87464F90AF547C83A81FF883 C6EAC281
Finally, check the status of FreeIPA services.
ipactl statusOutput:
Directory Service: RUNNING
krb5kdc Service: RUNNING
kadmin Service: RUNNING
named Service: RUNNING
ipa_memcached Service: RUNNING
httpd Service: RUNNING
pki-tomcatd Service: RUNNING
ipa-otpd Service: RUNNING
ipa: INFO: The ipactl command was successful
We have successfully installed a FreeIPA on CentOS 7.
The Kubernetes Book
$49.99 (as of July 9, 2025 21:12 GMT +00:00 – More infoProduct prices and availability are accurate as of the date/time indicated and are subject to change. Any price and availability information displayed on [relevant Amazon Site(s), as applicable] at the time of purchase will apply to the purchase of this product.)Conclusion – Install FreeIPA on CentOS 7
Installing FreeIPA on CentOS 7 opens up powerful capabilities for centralized identity management and authentication in your network environment. By following this guide, you should now have FreeIPA configured and ready to streamline user management and enhance security.
Your Linux servers deserve expert care! I provide reliable management and optimization services tailored to your needs. Discover how I can help on Fiverr!
Secure your network with FreeIPA today!




Leave a Reply
You must be logged in to post a comment.