Unlock the power of Kubernetes with our essential guide tailored for sysadmins! Discover step-by-step basics to master cluster management and boost your career today. Don’t get left behind—start learning Kubernetes now before your peers do! #centlinux #kubernetes #k8s
Table of Contents
Introduction to Kubernetes
In today’s fast-paced digital world, deploying and managing applications at scale isn’t just a technical necessity—it’s a competitive advantage. That’s where Kubernetes comes in.
Kubernetes, often abbreviated as K8s, is an open-source platform designed to automate the deployment, scaling, and operation of application containers. Originally developed by Google and now maintained by the Cloud Native Computing Foundation (CNCF), Kubernetes has become the de facto standard for container orchestration.
But what does that really mean?
Imagine you’re running several applications, each packaged in its own container (using tools like Docker). Managing one or two containers manually is simple—but what happens when you need to deploy hundreds or thousands of them, across dozens of servers, while ensuring they stay healthy, scale based on demand, and recover from failures automatically? Kubernetes handles all of this and more.
Here’s why Kubernetes is so popular:
- Automation: It handles repetitive tasks like rolling updates, failover, and resource allocation.
- Scalability: It can dynamically scale your applications up or down based on real-time usage.
- Resilience: If a container or server crashes, Kubernetes redeploys it automatically.
- Portability: It works across on-premises, hybrid, and multi-cloud environments, giving you flexibility and freedom.
In the realm of DevOps, K8s plays a vital role by enabling continuous integration and continuous deployment (CI/CD), infrastructure as code, and microservices architecture. It bridges the gap between development and operations by offering a unified platform for deploying and managing containerized applications with confidence and consistency.
Whether you’re just getting started with containers or looking to streamline your software delivery pipeline, learning Kubernetes is a game-changer. It empowers teams to move fast, stay agile, and deliver reliable software at scale.

Kubernetes Architecture
Kubernetes is like a smart operating system for your containerized applications. It helps you run, scale, and manage those applications reliably across a cluster of servers.
At the core of Kubernetes is a cluster, which is a set of machines (real or virtual) that work together. These machines are divided into two main types:
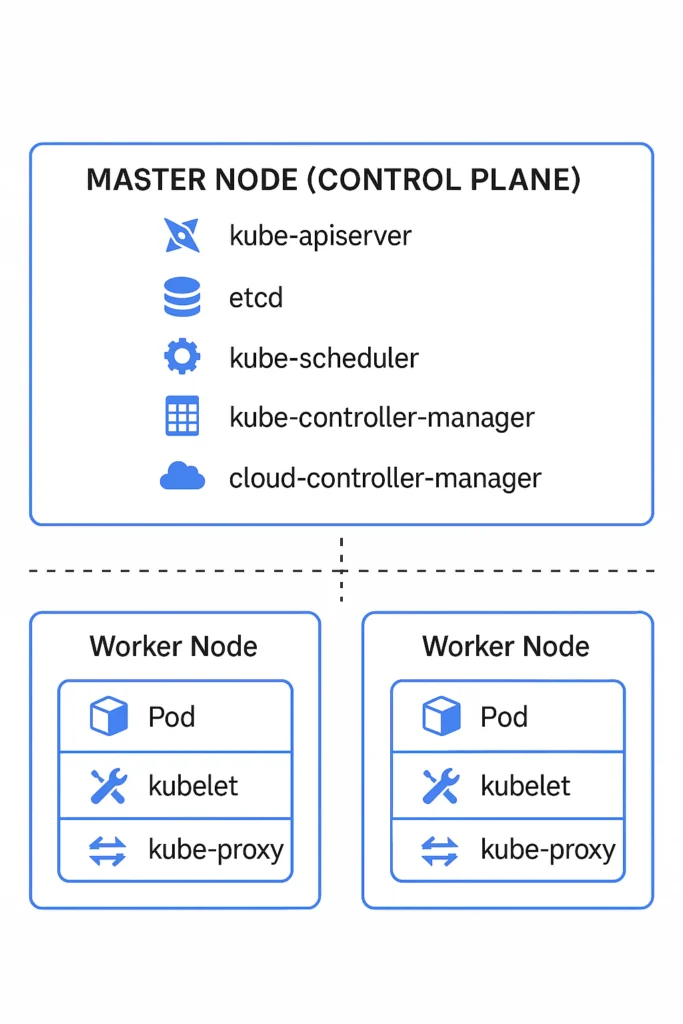
Master Node (Control Plane)
The master node is the brain of the K8s cluster. It’s responsible for making global decisions (like scheduling), detecting and responding to cluster events (like restarting a failed container), and maintaining the desired state of the system.
The control plane is made up of several components:
a. kube-apiserver
- The front door to the cluster.
- It’s how users and components communicate with Kubernetes.
- Accepts commands (usually via
kubectl), validates them, and sends them to the rest of the system.
b. etcd
- A fast, distributed key-value store that stores all cluster data.
- Think of it as Kubernetes’ memory—everything from node states to config data is stored here.
c. kube-scheduler
- Decides which node runs a newly created pod.
- It considers factors like resource availability, affinity rules, and workload.
d. kube-controller-manager
- Watches over the cluster and makes sure everything is running as desired.
- Contains various controllers, like:
- Node Controller: Checks node health.
- Replication Controller: Ensures the desired number of pods are running.
- Endpoints Controller: Connects Services to Pods.
e. cloud-controller-manager (optional)
- Manages cloud-specific resources (like load balancers or storage volumes) when Kubernetes is running in a cloud environment.
Analogy: Think of the master node as a city planner who decides where buildings (pods) go, ensures the power grid (network) is connected, and keeps records of everything.
If you’re eager to kickstart your journey into cloud-native technologies, “Kubernetes for the Absolute Beginners – Hands-on” by Mumshad Mannambeth is the perfect course for you. Designed for complete beginners, this course breaks down complex concepts into easy-to-follow, hands-on lessons that will get you comfortable deploying, managing, and scaling applications on Kubernetes.
Whether you’re a developer, sysadmin, or IT enthusiast, this course provides the practical skills needed to confidently work with Kubernetes in real-world scenarios. By enrolling through the links in this post, you also support this website at no extra cost to you.
Disclaimer: Some of the links in this post are affiliate links. This means I may earn a small commission if you make a purchase through these links, at no additional cost to you.
Worker Nodes (Minions)
These are the machines where your actual applications run.
Each worker node contains:
a. kubelet
- A small agent that runs on each node.
- Talks to the control plane and makes sure the containers described in the PodSpec are running.
b. kube-proxy
- Manages networking rules on each node.
- Ensures network traffic is routed correctly between services and pods.
c. Container runtime
- Software like Docker or containerd that actually runs the containers.
Analogy: Think of worker nodes as construction sites where buildings (pods) are actually constructed and maintained under the supervision of a local foreman (kubelet).
Core Concepts in Kubernetes
Pods
- The smallest unit of deployment in Kubernetes.
- A Pod can hold one or more containers that share the same network and storage.
- If your app needs a sidecar (e.g., a logging agent or proxy), both can run in the same pod.
Example: A pod could run a single NGINX web server, or a web server + a logging agent.
Deployments
- A high-level abstraction that manages Pods and ReplicaSets.
- Allows you to declaratively update, rollback, and scale your apps.
Example: A Deployment might define that 3 replicas of your web app should always be running. If one crashes, Kubernetes will replace it automatically.
Services
- Kubernetes pods have dynamic IPs, so you can’t reliably connect to them directly.
- A Service gives a stable endpoint (IP and DNS name) to access a group of pods.
Types of services
- ClusterIP (default): Internal access only.
- NodePort: Exposes service on a static port on each node.
- LoadBalancer: Integrates with cloud providers to create external load balancers.
Analogy: Services are like reception desks that help you find and connect to a group of employees (pods) even if they change desks (IP addresses) regularly.
Read Also: KYAML: Complete Guide to Kubernetes YAML
Example Workflow
Let’s say you want to deploy a Node.js app:
- You create a Deployment that specifies the app container image, number of replicas, and update strategy.
- The scheduler places your Pods (containers) on available worker nodes.
- You create a Service to allow users to access the app reliably.
- Kubernetes monitors the app and automatically restarts pods if they fail, reschedules them if a node goes down, and scales them if traffic increases.
Architecture Diagram
In Summary
| Component | Role |
|---|---|
| Master Node | Controls the cluster |
| Worker Node | Runs the actual workloads (pods) |
| Pod | Smallest deployable unit (contains container/s) |
| Service | Provides stable access to pods |
| Deployment | Manages pod lifecycles and scaling |
By mastering K8s architecture, you gain the power to orchestrate containers at scale, automate recovery, and build highly reliable infrastructure—the cornerstone of modern DevOps.
Read Also: GKE vs EKS vs AKS: Choose Right Kubernetes Service
Kubernetes Installation Methods
Online Installation
This method downloads required packages, images, and dependencies directly from the internet during installation.
Pros:
- Easier and faster setup.
- Always uses the latest stable packages.
- Ideal for internet-connected environments.
Cons:
- Requires reliable internet access.
- Slower in air-gapped or firewalled environments.
Offline Installation
Packages, container images, and dependencies are pre-downloaded and transferred to target machines manually.
Pros:
- Works in air-gapped, secure, or isolated environments.
- More control over package versions.
Cons:
- More complex and time-consuming.
- Needs careful preparation and testing.
Guide: How to install Kubernetes offline on CentOS 7
Kubernetes Installation by Linux Distribution
1. Ubuntu Server
Ubuntu is one of the most popular platforms for Kubernetes due to its developer-friendly nature and LTS support.
Online Installation Methods:
kubeadm(official method): Straightforward setup.snapinstall of MicroK8s (single-node/local clusters).- Minikube (for local development and testing).
Guide: How to install Kubernetes on Ubuntu Server 18
2. Rocky Linux
Rocky Linux is a CentOS replacement, often used in enterprise environments.
Online Installation Methods:
kubeadmwith CRI-O or containerd.- SELinux-compatible configuration for production readiness.
Guide: How to install Kubernetes on Rocky Linux 9
3. CentOS
Though CentOS 7 is aging, it’s still widely used in legacy environments.
Offline Installation:
- Pre-download RPMs, Kubernetes binaries, and container images.
- Set up local repo or shared mount.
- Useful for data centers without internet access.
Guide: How to setup Kubernetes Cluster on CentOS 7
Choosing the Right Method
| Scenario | Recommended Method |
|---|---|
| Learning or testing | Minikube |
| Cloud/production setup | Hostinger VPS |
| Enterprise air-gapped env | kubeadm |
| Lightweight clusters | MicroK8s / K3s |
Kubernetes Security Best Practices
1. Role-Based Access Control (RBAC)
What it is
RBAC is a fine-grained authorization mechanism in Kubernetes that controls who can perform what actions on which resources in a cluster.
Why it matters
Without RBAC, any user or service could potentially have unrestricted access to your Kubernetes resources, increasing the risk of accidental or malicious changes.
Best practices
- Least privilege principle: Assign the minimum permissions necessary for users and service accounts to perform their tasks.
- Use roles and role bindings: Create Roles (namespace-scoped) and ClusterRoles (cluster-wide) to group permissions logically, then bind these to users or service accounts.
- Separate duties: Differentiate roles for administrators, developers, CI/CD pipelines, and external services.
- Audit and review regularly: Continuously monitor role bindings and permissions to detect and remove unnecessary privileges.
2. Transport Layer Security (TLS)
What it is
TLS is a cryptographic protocol that secures communications by encrypting data transmitted between clients, Kubernetes API server, kubelets, etc.
Why it matters:
Kubernetes components communicate over the network frequently. TLS ensures this communication is encrypted and authenticated, preventing man-in-the-middle attacks and eavesdropping.
Best practices
- Enable TLS for all API server endpoints: Kubernetes API server should be configured to serve over HTTPS only.
- Use strong, trusted certificates: Use certificates issued by a trusted Certificate Authority (CA). For internal cluster communication, use your own CA.
- Rotate certificates regularly: Renew and replace certificates before expiration.
- Secure kubelet communication: Ensure kubelets serve endpoints over TLS and authenticate requests.
- Use Mutual TLS where possible: Both client and server verify each other’s identity, especially for inter-cluster communications.
3. Secret Encryption at Rest
What it is
By default, Kubernetes stores Secrets as base64-encoded data in etcd, which is not encrypted and can be exposed if etcd storage is compromised.
Why it matters
Secrets often contain sensitive data such as passwords, tokens, and keys. Encrypting these at rest protects them even if the storage backend (etcd) is breached.
Best practices
- Enable encryption providers for Secrets: Kubernetes supports encrypting Secret data in etcd using built-in encryption providers.
- Use strong encryption algorithms: AES-CBC or AES-GCM are recommended.
- Manage encryption keys carefully: Rotate encryption keys periodically, and keep old keys to enable decryption of previously encrypted data.
- Audit access: Monitor access to etcd and the API server to detect unauthorized access attempts.
Summary
Why Encrypt Secrets at Rest?
- Protects sensitive data in etcd from exposure if someone gains direct access.
- Adds an additional security layer beyond network encryption.
- Helps meet compliance and regulatory requirements for data protection.
How to Implement Secret Encryption at Rest
Create an encryption configuration file:
Define which resources (like Secrets) to encrypt and specify encryption providers and keys. Example snippet (encryption-config.yaml):
apiVersion: apiserver.config.k8s.io/v1
kind: EncryptionConfiguration
resources:
- resources:
- secrets
providers:
- aescbc:
keys:
- name: key1
secret: <base64-encoded-32-byte-secret>
- identity: {}Configure the API server:
Pass the --encryption-provider-config flag pointing to the above file when starting the kube-apiserver.
Restart the API server:
Apply the configuration change by restarting the control plane component.
Re-encrypt existing Secrets:
Existing Secrets are not automatically re-encrypted; you may need to re-create them or run a manual re-encryption process.
Guide: Kubernetes Secrets Encryption: A Practical Guide
Kubernetes Alternatives
1. Architecture
| Aspect | Kubernetes | Docker Swarm | HashiCorp Nomad |
|---|---|---|---|
| Core Model | Master-worker architecture with control plane components (API server, scheduler, controller manager) and worker nodes running kubelet and container runtime. | Manager-worker architecture integrated with Docker Engine, where managers handle orchestration and workers run containers. | Single binary orchestrator with a client-server model, agents run on all nodes, no separate control plane components. |
| Container Runtime | Supports multiple runtimes (containerd, CRI-O, Docker, etc.) | Docker Engine by default | Supports Docker, containerd, rkt, and other runtimes via plugins. |
| Scheduling | Complex scheduler with rich features like affinity, taints, tolerations, priority, and custom schedulers. | Simpler scheduler focused on Docker containers, supports constraints and service placement. | Flexible scheduler with batch, system, and service jobs; supports multi-region and multi-cloud. |
| Networking | Uses Container Network Interface (CNI) plugins for flexible, pluggable networking, supports overlay networks and advanced policies. | Built-in overlay networking with automatic service discovery using DNS. | Integrates with Consul for service discovery and networking; supports flexible networking setups. |
| Storage | Supports multiple volume types via plugins and CSI drivers, persistent volumes, dynamic provisioning. | Supports Docker volumes and plugins but less sophisticated than Kubernetes. | Integrates with various storage systems; not as feature-rich as Kubernetes. |

2. Ease of Use
| Aspect | Kubernetes | Docker Swarm | HashiCorp Nomad |
|---|---|---|---|
| Setup Complexity | Steep learning curve; complex to install and configure; many moving parts. | Very easy to set up; native to Docker CLI; minimal configuration. | Simple installation with a single binary; easier than Kubernetes but requires HashiCorp stack knowledge. |
| User Experience | Rich but complex API, requires familiarity with many concepts (pods, deployments, services). | Simple Docker CLI commands; integrates well with existing Docker workflows. | Declarative job specifications in HCL (HashiCorp Configuration Language), easier for ops familiar with HashiCorp tools. |
| Learning Curve | High; steep learning curve due to extensive features and ecosystem. | Low; good for Docker users who want basic orchestration. | Moderate; easier than Kubernetes but requires learning Nomad-specific concepts and HCL. |
Guide: Hashicorp Nomad vs Kubernetes
3. Scalability
| Aspect | Kubernetes | Docker Swarm | HashiCorp Nomad |
|---|---|---|---|
| Cluster Size | Designed for very large clusters (thousands of nodes), production-grade scalability. | Suitable for small to medium clusters (hundreds of nodes max). | Designed for large scale and multi-region clusters; thousands of nodes supported. |
| Workload Types | Supports complex workloads, stateful sets, batch jobs, cron jobs, and more. | Primarily for stateless and simple workloads; limited support for stateful. | Supports batch, service, and system workloads with advanced scheduling features. |
| Resilience | Highly resilient with automatic failover, self-healing, and replication. | Good resilience but less robust than Kubernetes in complex scenarios. | Strong resilience, supports multi-region failover and flexible job rescheduling. |
4. Real-World Use Cases
| Tool | Use Cases |
|---|---|
| Kubernetes | Large-scale microservices, hybrid/multi-cloud deployments, complex CI/CD pipelines, stateful applications, big enterprises. |
| Docker Swarm | Small to medium projects, startups, simple container orchestration, developers already invested in Docker who want quick orchestration. |
| HashiCorp Nomad | Organizations already using HashiCorp tools (Consul, Vault, Terraform), multi-cloud or multi-datacenter orchestration, batch processing, mixed workload types including VMs, containers, and standalone apps. |
5. Guidance: When to Choose Which?
| Scenario | Recommended Tool | Reason |
|---|---|---|
| You need enterprise-grade orchestration with extensive ecosystem and community support | Kubernetes | Best for complex, scalable, and production workloads with a rich ecosystem and flexibility. |
| You want simple container orchestration and fast setup with minimal overhead | Docker Swarm | Ideal for small teams or projects that already use Docker and want to orchestrate containers simply. |
| You want flexible workload orchestration beyond just containers and integrate with HashiCorp tools | HashiCorp Nomad | Great if you need batch jobs, multi-cloud, multi-region support, and infrastructure-as-code integration. |
Guide: Docker Swarm vs Kubernetes
Summary
| Tool | Pros | Cons |
|---|---|---|
| Kubernetes | Powerful, extensible, huge ecosystem | Complex to set up and manage |
| Docker Swarm | Easy to use, tightly integrated with Docker | Limited features and scalability compared to Kubernetes |
| HashiCorp Nomad | Lightweight, supports mixed workloads, easy to deploy | Smaller community, fewer out-of-the-box integrations |
Kubernetes Cluster Setup and Best Practices
1. Cluster Setup and Architecture
- Use the Latest Stable Version: Always deploy the latest stable K8s version for security patches and new features.
- Multi-Master High Availability:
- Deploy multiple control plane (master) nodes across different availability zones or data centers to avoid single points of failure.
- Use an external etcd cluster or a highly available etcd setup with at least 3 nodes.
- Network Design:
- Use a robust CNI plugin (e.g., Calico, Flannel, Cilium) for network overlay.
- Ensure pod network CIDR is planned to avoid overlaps with other networks.
- Security Hardening:
- Enable Role-Based Access Control (RBAC) with least privilege principles.
- Use TLS encryption for all API communications.
- Limit kubelet permissions on worker nodes.
- Regularly update and patch nodes and cluster components.
2. High Availability (HA)
- Control Plane HA:
- Deploy at least 3 control plane nodes.
- Use a load balancer (e.g., HAProxy, AWS ELB) to distribute API server traffic.
- etcd HA:
- Maintain an odd number of etcd nodes (3 or 5) for quorum-based fault tolerance.
- Use backup and restore mechanisms for etcd data.
- Worker Node HA:
- Spread worker nodes across multiple zones or racks to avoid correlated failures.
- Pod and Service HA:
- Use Deployments, ReplicaSets, and StatefulSets with multiple replicas.
- Enable PodDisruptionBudgets to maintain minimum available pods during maintenance.
3. Node Scaling
- Horizontal Pod Autoscaling (HPA):
- Automatically scale pods based on CPU/memory or custom metrics.
- Cluster Autoscaler:
- Automatically add/remove nodes based on pod resource requests and usage.
- Integrate with cloud provider APIs for dynamic scaling.
- Right-Sizing Nodes:
- Choose node instance types that match workload resource profiles.
- Mix node pools (e.g., GPU, high-memory, standard) for diverse workloads.
- Resource Requests and Limits:
- Define resource requests and limits for every container to optimize scheduling and prevent resource contention.
4. Logging
- Centralized Logging System:
- Deploy log collectors like Fluentd, Logstash, or Fluent Bit to aggregate logs.
- Ship logs to centralized storage like Elasticsearch, Loki, or cloud logging services.
- Structured Logs:
- Use structured JSON logging in applications to facilitate filtering and analysis.
- Retention and Rotation:
- Implement log retention policies to avoid storage bloat.
- Use log rotation on nodes to prevent disk saturation.
- Cluster and Application Logs:
- Collect Kubernetes system logs (API server, scheduler, controller-manager).
- Collect application and container logs via sidecars or node agents.
5. Monitoring
- Cluster Monitoring:
- Use Prometheus for metrics collection from nodes, pods, and Kubernetes components.
- Visualize metrics with Grafana dashboards.
- Node and Pod Health:
- Monitor node resource usage (CPU, memory, disk, network).
- Track pod status, restarts, and failures.
- Alerting:
- Define alerting rules for critical conditions (node down, high resource usage, pod failures).
- Integrate with notification systems (Slack, PagerDuty, email).
- Application Monitoring:
- Implement application-level instrumentation with tools like OpenTelemetry.
- Monitor business KPIs alongside infrastructure metrics.
6. Backup Strategies
- etcd Backups:
- Schedule regular etcd snapshots and test restoration processes.
- Store backups securely and offsite.
- Persistent Volume (PV) Backups:
- Use volume snapshot tools compatible with your storage backend (e.g., CSI snapshots).
- Regularly backup PV data especially for databases and stateful apps.
- Cluster State Backup:
- Backup Kubernetes manifests, ConfigMaps, Secrets, and RBAC configurations via GitOps or tools like Velero.
- Disaster Recovery:
- Have tested runbooks for cluster rebuild and data restoration.
- Automate recovery processes as much as possible.
- Secret Management:
- Store and backup secrets securely using tools like Sealed Secrets or HashiCorp Vault.
Summary Table
| Aspect | Best Practices Summary |
|---|---|
| HA | Multi-master control plane, etcd quorum, load balancer |
| Node Scaling | HPA, Cluster Autoscaler, resource limits, node right-sizing |
| Logging | Centralized logging (Fluentd/Elastic), structured logs, retention |
| Monitoring | Prometheus + Grafana, alerting, node/pod health tracking |
| Backup | Regular etcd & PV backups, cluster state backup, disaster recovery |
Frequently Asked Questions (FAQs)
1. What is Kubernetes and why should sysadmins care?
Kubernetes is an open‑source container orchestration platform that automates deployment, scaling, and management of containerized applications. For sysadmins, it provides a standardized way to manage infrastructure, improve resource utilization, and ensure high availability of services.
2. What are the core components of a Kubernetes cluster?
A Kubernetes cluster consists of:
– Control Plane (API Server, Controller Manager, Scheduler, etcd) which manages the desired state.
– Worker Nodes that run the containerized workloads (via kubelet and kube‑proxy).
– etcd as the key‑value store for all cluster data.
Understanding these roles helps sysadmins troubleshoot and maintain cluster health.
3. How do I ensure high availability for critical services?
Key strategies include running multiple replicas of your Pods behind a Service, distributing nodes across failure domains (zones/racks), and configuring liveness/readiness probes so Kubernetes can automatically replace unhealthy containers.
4. What basic networking concepts should I know?
You should understand:
– Pod-to-Pod networking (flat network where every Pod can reach every other Pod).
– Services (stable IPs and DNS names for sets of Pods).
– Network Policies (rules to control traffic).
Familiarity with CNI plugins (Calico, Flannel, etc.) will guide network setup and troubleshooting.
5. How can I monitor and log my cluster effectively?
Implement a metrics stack (e.g., Prometheus + Grafana) for resource and performance monitoring, and a centralized logging solution (e.g., Elasticsearch, Fluentd, Kibana). This lets you track cluster health, alert on anomalies, and debug issues by examining logs across nodes and Pods.
Conclusion
Kubernetes has revolutionized the way modern organizations manage, scale, and automate their infrastructure. By abstracting complex container orchestration tasks, K8s enables teams to deploy applications faster, maintain high availability, and efficiently utilize resources—all while supporting continuous integration and continuous delivery (CI/CD) pipelines. Its extensible architecture, rich ecosystem, and declarative management model empower developers and operators alike to automate routine operational tasks, reduce downtime, and improve system resilience. As cloud-native adoption continues to grow, Kubernetes remains a foundational technology that drives agility, scalability, and reliability in infrastructure automation.
Embracing Kubernetes means embracing a future where infrastructure is code, workflows are automated, and applications seamlessly adapt to demand — making it an indispensable tool for businesses aiming to innovate rapidly while maintaining operational excellence.
Whether you need cloud optimization, server management, or automation, I provide comprehensive AWS and Linux services. Hire me to elevate your systems.
Helpful Resources and Tutorials for Kubernetes
Official Documentation & Learning
- Kubernetes Official Documentation
- Kubernetes Basics Interactive Tutorial
- Certified Kubernetes Administrator (CKA) Curriculum
Tutorials and Guides
- Kubernetes Secrets Encryption: A Practical Guide
- Ultimate Guide to Minikube Clusters
- How to setup k3s Cluster on k3OS
Cheat Sheets
- Kubernetes kubectl Cheat Sheet
- Kubernetes API Resources and Commands Cheat Sheet
- Kubernetes Networking Cheat Sheet

Leave a Reply
You must be logged in to post a comment.