Unlock faster, password-free logins now! Learn how to set up SSH keys in PuTTY and secure your remote connections like a pro—before you’re left behind. Discover the step-by-step guide that developers rely on to boost productivity and tighten security! #centlinux #linux #ssh
Table of Contents
What are SSH Keys?
SSH keys are a pair of cryptographic keys used for authenticating and securing SSH (Secure Shell) connections. SSH keys provide a more secure and convenient alternative to password-based authentication. Here’s an overview of SSH keys and their functionality:
Key Concepts
- Public and Private Keys:
- Private Key: Kept secret and stored securely on the user’s local machine. This key should never be shared.
- Public Key: Shared with the remote server you wish to access. This key can be distributed without compromising security.
- How They Work:
- When you attempt to connect to a remote server, the server uses the public key to create a challenge message that only the corresponding private key can decrypt.
- If your local machine successfully decrypts the challenge using the private key, the server grants access.
- Key Pairs:
- SSH keys are generated in pairs using cryptographic algorithms like RSA, DSA, or ECDSA. These algorithms ensure that the keys are mathematically linked but cannot be feasibly reverse-engineered.

Advantages of SSH Keys
- Security:
- SSH keys provide strong authentication and are virtually immune to brute-force attacks.
- Using SSH keys eliminates the risk of password theft, especially through phishing attacks.
- Convenience:
- Once set up, SSH keys allow for passwordless logins, which simplifies the process of accessing remote servers.
- SSH keys can be used for automating tasks that require SSH connections, without the need to store plaintext passwords.
- Flexibility:
- SSH keys can be used with various SSH clients and servers across different operating systems.
- Multiple public keys can be added to a single server account, allowing multiple users or devices to access the same account securely.
Potential Issues
- Security Risks:
- If the private key is compromised, unauthorized users can gain access to your accounts. It’s crucial to protect your private key with a strong passphrase and secure storage.
- Users should regularly rotate their keys and remove unused public keys from servers.
- Configuration Complexity:
- Setting up SSH keys requires some technical knowledge and can be confusing for beginners.
- Misconfigurations can lead to access issues, requiring careful attention to detail.
SSH keys are a powerful and secure method for authenticating SSH connections. They provide enhanced security and convenience over traditional password-based logins. By understanding and properly managing SSH keys, users can significantly improve the security of their remote server access.
Recommended Courses
Boost your Linux and network security skills with “Secure Shell (SSH) Essentials: A Hands-On Guide” by Ahmed Elfakharany. This course walks you step by step through mastering SSH, from secure server access to advanced command-line techniques, making it perfect for system administrators, developers, and tech enthusiasts looking to level up their security game.
With practical exercises and real-world examples, you’ll gain hands-on experience that you can immediately apply. Don’t miss this opportunity to strengthen your SSH expertise—enroll now through my affiliate link and start mastering SSH today! (Disclaimer: Some of the links in this post are affiliate links, which means I may earn a small commission at no extra cost to you if you make a purchase through them. Your support helps me keep providing valuable content!)
Problem Statement
PuTTY is a free and open-source SSH and telnet client. It is primarily developed by Simon Tatham for Microsoft Windows but now it supports a wide variety of other operating systems. Public key authentication is a feature of PuTTY, in which, we can configure SSH Keys to allow password less logins to Linux machines from our PuTTY terminals.
In this article, we will setup SSH Keys in PuTTY by using PuTTYgen and then configure a CentOS 7 machine for password less logins by SSH client.
Environment Specification
One Microsoft Windows based client and a CentOS 7 based server.
Read Also: Configure SSH Passwordless Logins between Linux servers
Generate SSH Keys using PuTTYgen
PuTTYgen is included with PuTTY SSH client. Both are free and open source and distributed under MIT License. Therefore, it is available for free download at PuTTY official website.
We have already installed PuTTY SSH client on our MS Windows client.
Search and run PuTTYgen application.
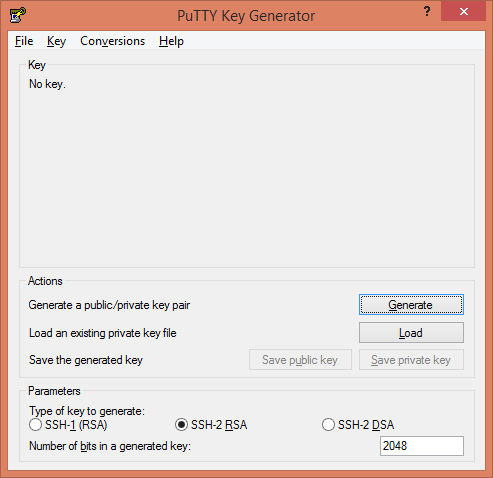
Click on Generate button to generate a SSH Public/Private keys pair.
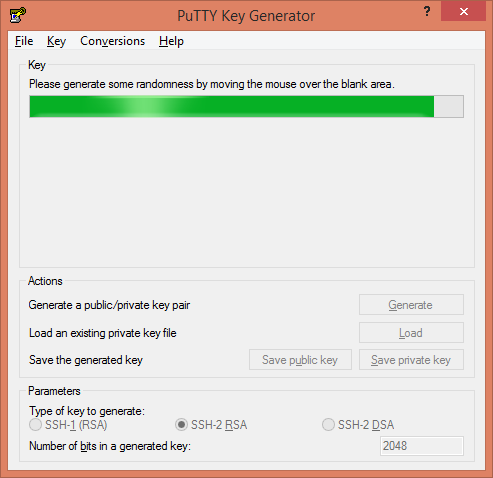
Meanwhile, we are required to scroll mouse in the area under the progress bar for randomization and generation of SSH Keys.
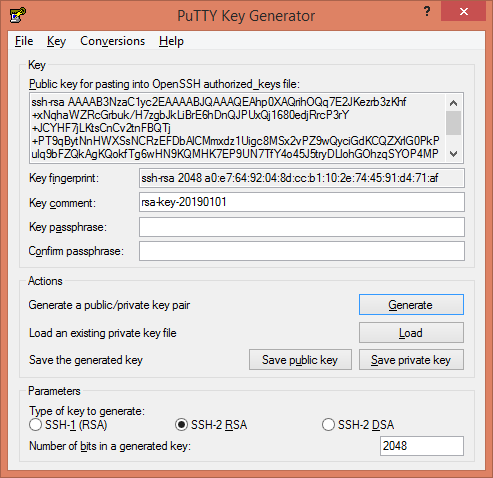
PuTTYgen has generated a SSH Public/Private keys pair.
Click on Save private key button to save the SSH Private Key locally.
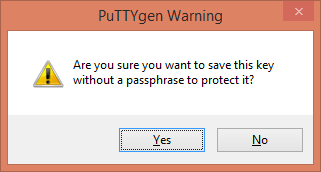
Since, we are not defining any passphrase, therefore, PuTTYgen is displaying the above warning.
Ignore it and click on Yes.
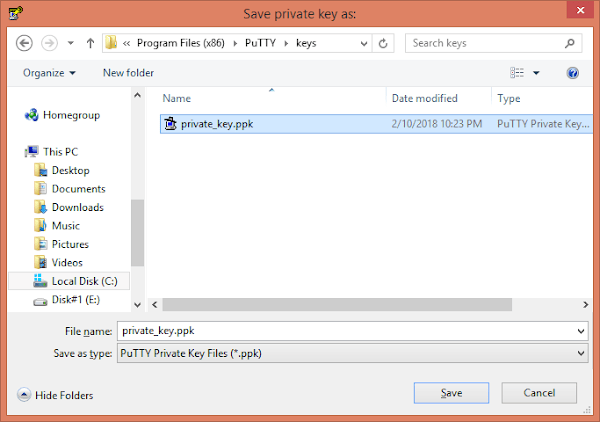
We have saved our Private SSH Key in a local directory. You can also save your Public SSH Key in the same way, if you plan to use this same SSH Keys pair for more than one Linux machines.
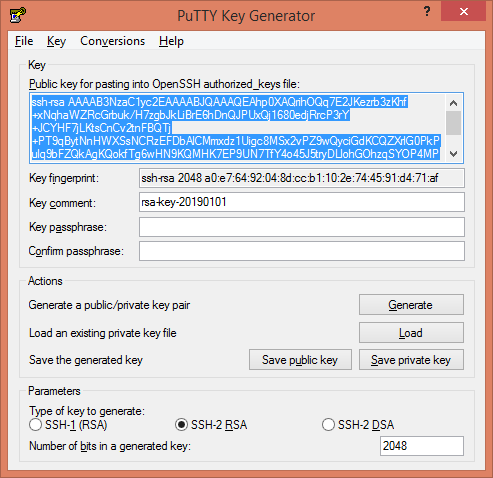
Select the generated SSH Public Key and copy it to clipboard.
Setup SSH Keys in PuTTY
Connect to our CentOS 7 machine using PuTTY and insert SSH Public Key in ~/.ssh/authorized_keys file.
mkdir ~/.ssh
vi ~/.ssh/authorized_keys
exitNow, open PuTTY and add a session for that CentOS 7 server.
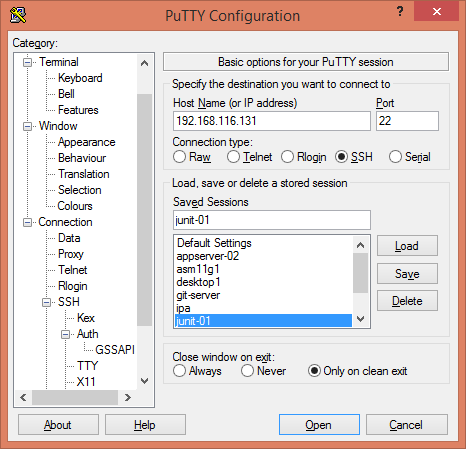
Besides other settings, we are required to include our Private SSH Key as follows:
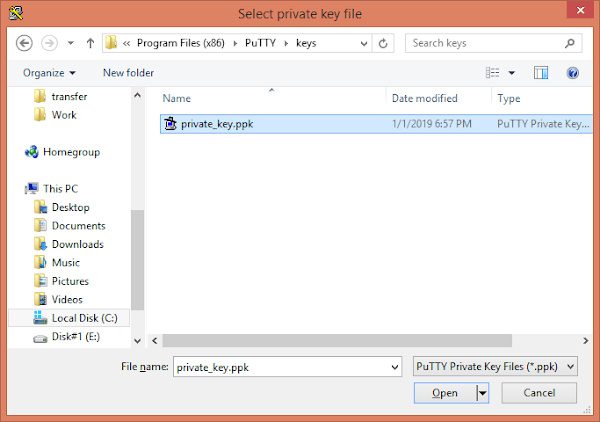
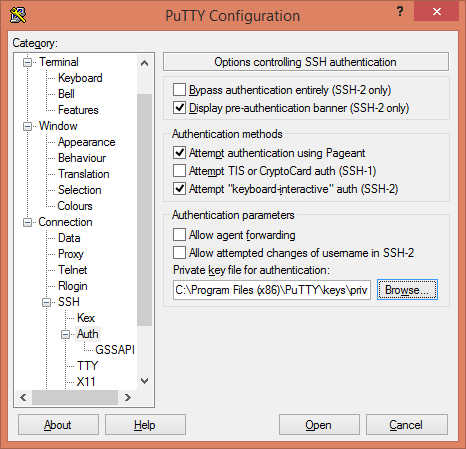
Save first and then open this session.
login as: root Authenticating with public key "rsa-key-20190101" Last login: Tue Jan 1 18:59:44 2019 from 192.168.116.1 #
Our CentOS 7 server won’t prompt for a password this time.
Final Thoughts
Now that you’ve learned how to set up SSH keys in PuTTY, you’re equipped with a faster, more secure way to access your remote servers—no more fumbling with passwords! By generating key pairs and configuring PuTTY and PuTTYgen correctly, you’ve taken a critical step toward streamlining your workflow and protecting your infrastructure.
Don’t wait until a security breach or login delay slows you down—start using SSH keys today and stay ahead of the curve. Thousands of developers and sysadmins already rely on this setup—why not you?
Searching for a skilled Linux admin? From server management to security, I ensure seamless operations for your Linux systems. Find out more on my Freelancer profile!
Let’s ensure your remote connections are secure and efficient!
