In this tutorial, you will learn, how to install OpenSCAP tool on Rocky Linux 9 and run Vulnerability Scan on your Linux Operating System. #centlinux #linux #openscap
Table of Contents
What is OpenSCAP?
In today’s digital landscape, with new threats emerging daily, regular scanning of your Linux servers is essential. OpenSCAP (Security Content Automation Protocol) is an open-source framework designed for managing security compliance checking, vulnerability management, and policy enforcement. It provides a standardized approach for maintaining system security and compliance with various security policies, benchmarks, and guidelines.
Key components of OpenSCAP tool include:
- SCAP Content: OpenSCAP Scanner provides a collection of security policies, benchmarks, and guidelines in the form of SCAP (Security Content Automation Protocol) content. This content is based on various standards such as Common Vulnerabilities and Exposures (CVE), Common Configuration Enumeration (CCE), Common Platform Enumeration (CPE), Common Vulnerability Scoring System (CVSS), etc.
- Scanner: OpenSCAP tool includes a scanner component that can assess the security posture of systems by evaluating them against predefined security policies and benchmarks. The scanner can check for vulnerabilities, misconfigurations, and adherence to security best practices.
- Utilities: OpenSCAP tool provides various command-line utilities and APIs for interacting with SCAP content, running scans, generating reports, and integrating it’s functionality into other security management tools and systems.
- Reporting: OpenSCAP scanner generates detailed reports after scanning systems, providing information on security vulnerabilities, compliance status, and recommendations for remediation. These reports help system administrators and security professionals to identify and address security issues effectively.
- Integration: OpenSCAP tool can be integrated with other security tools and systems, such as configuration management systems, security information and event management (SIEM) solutions, and vulnerability management platforms, to enhance overall security management capabilities.
OpenSCAP scanner is widely used in enterprise environments, government agencies, and other organizations to ensure the security and compliance of their IT infrastructure, including servers, workstations, and cloud environments. It helps organizations automate security assessments, streamline compliance efforts, and improve overall security posture.

How to perform OpenSCAP Vulnerability Scan?
An OpenSCAP vulnerability scan is a process where the OpenSCAP tool is utilized to assess the security posture of a system or a network by scanning for vulnerabilities, misconfigurations, and adherence to security policies and standards. Here’s an overview of how an OpenSCAP vulnerability scan typically works:
Preparation: Before initiating the scan, the user typically selects or defines the security benchmarks, policies, or standards against which the system will be evaluated. These benchmarks may include industry standards like CIS (Center for Internet Security), DISA STIGs (Defense Information Systems Agency Security Technical Implementation Guides), or other custom policies.
Read Also: STIG Automation with Ansible Playbooks
Scanning: The OpenSCAP scanner then conducts the scan based on the selected benchmarks and policies. It checks various aspects of the system configuration, including but not limited to:
- Presence of known vulnerabilities (identified by CVE IDs)
- Configuration settings that deviate from best practices or security standards
- Compliance with specific security requirements outlined in the selected benchmarks
Evaluation: During the scan, OpenSCAP tool evaluates the system’s configuration and settings against the predefined benchmarks and policies. It identifies vulnerabilities, weaknesses, and areas of non-compliance.
Reporting: Once the scan is completed, OpenSCAP generates a detailed report summarizing the findings. This report typically includes:
- List of vulnerabilities detected, along with their severity ratings and CVE identifiers
- Configuration issues and deviations from security best practices
- Compliance status with respect to the selected benchmarks or standards
- Recommendations for remediation, including steps to mitigate identified vulnerabilities and improve overall security posture
Remediation: Based on the findings of the vulnerability scan, system administrators and security professionals can take appropriate actions to address the identified issues. This may involve applying software patches, reconfiguring system settings, or implementing additional security controls to mitigate risks and improve security.
Overall, an OpenSCAP vulnerability scan provides organizations with valuable insights into the security status of their systems, helping them identify and prioritize security risks, comply with regulatory requirements, and enhance their overall security posture.
If you are serious about starting your journey in cybersecurity, I highly recommend the “Learn Ethical Hacking From Scratch” by Zaid Sabih course. Designed for beginners, this hands-on course walks you through real-world hacking techniques and security practices, giving you the skills to think like a hacker while defending against them.
It’s one of the top-rated courses in the industry, trusted by thousands of learners worldwide, and a perfect choice if you want to build a career in penetration testing or simply secure your own digital footprint. You can [enroll today] through my affiliate link and start learning step by step from scratch.
Disclaimer: This post contains affiliate links. If you make a purchase through these links, I may earn a small commission at no additional cost to you. This helps support my blog and allows me to continue creating valuable content.)
Environment Specification
We are using a minimal Rocky Linux 9 virtual machine with following specifications.
- CPU – 3.4 Ghz (2 cores)
- Memory – 4 GB
- Storage – 40 GB
- Operating System – Rocky Linux release 9.3 (Blue Onyx)
- Hostname – openscap-01.centlinux.com
- IP Address – 192.168.18.121/24
For those looking to set up a similar environment for experimenting with Linux installations like OpenSCAP, using a compact Mini PC or a reliable VPS can be an excellent choice.
A Mini PC offers the advantage of dedicated hardware with low power consumption and quiet operation, making it ideal for a personal lab or home server. I recommend checking out options available on Amazon that balance performance and affordability.
Alternatively, if you prefer a cloud-based solution with scalable resources and easy remote access, consider VPS providers such as Bluehost or Rose Hosting. Both offer VPS plans well-suited for running Rocky Linux 9 and other Linux distributions, enabling flexible, always-on environments for testing, development, and security scans.
Read Also: How to Reset Root Password in Kali Linux
Pre-installation Configuration
Login to your Rocky Linux Server as a privileged user by using any ssh client.
Set hostname for your Linux machine and configure local DNS resolution as follows.
# hostnamectl set-hostname openscap-01.centlinux.com
# echo 192.168.18.121 openscap-01 openscap-01.centlinux.com >> /etc/hostsUpdate Linux software packages by executing following command.
# dnf update -yThe above command may also update software packages related to Linux Kernel. In such case, reboot your Linux machine before moving forward.
# rebootCheck the Linux OS & Linux Kernel version.
# cat /etc/os-release
NAME="Rocky Linux"
VERSION="9.3 (Blue Onyx)"
ID="rocky"
ID_LIKE="rhel centos fedora"
VERSION_ID="9.3"
PLATFORM_ID="platform:el9"
PRETTY_NAME="Rocky Linux 9.3 (Blue Onyx)"
ANSI_COLOR="0;32"
LOGO="fedora-logo-icon"
CPE_NAME="cpe:/o:rocky:rocky:9::baseos"
HOME_URL="https://rockylinux.org/"
BUG_REPORT_URL="https://bugs.rockylinux.org/"
SUPPORT_END="2032-05-31"
ROCKY_SUPPORT_PRODUCT="Rocky-Linux-9"
ROCKY_SUPPORT_PRODUCT_VERSION="9.3"
REDHAT_SUPPORT_PRODUCT="Rocky Linux"
REDHAT_SUPPORT_PRODUCT_VERSION="9.3"
# uname -r
5.14.0-362.18.1.el9_3.0.1.x86_64Install OpenSCAP Tool on Rocky Linux 9
You will require, following two packages to install OpenSCAP tool and run vulnerability scan from Linux command line. Both of these packages are available in standard yum repositories.
# dnf install -y openscap-scanner scap-security-guideHere,
- openscap-scanner package provides the oscap command.
- scap-security-guide provides the Security Policies.
You can optionally install scap-workbench package, if you wish to use OpenSCAP from graphical interface.
Read Also: How to install OpenVAS on Rocky Linux 9
Select a Security Policy
SSG (SCAP Security Guide) policy files are located in the /usr/share/xml/scap/ssg/content/ directory.
You can execute following command to get list of SSG policy files.
# ls -1 /usr/share/xml/scap/ssg/content/ssg-*-ds.xml
/usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
/usr/share/xml/scap/ssg/content/ssg-rl9-ds.xmlSelect a Security Profile
Each security policy can have multiple profiles which provide policies implemented according to specific security baselines. Every profile can select different rules and use different values. You can list these profiles using the following command:
# oscap info /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml [
Document type: Source Data Stream
Imported: 2024-02-26T20:55:34
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-rhel9-xccdf.xml
Generated: (null)
Version: 1.3
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-xccdf.xml
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-v2-RHEL9-rhel-9.oval.xml.bz2' points out to the remote 'https://access.redhat.com/security/data/oval/v2/RHEL9/rhel-9.oval.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://access.redhat.com/security/data/oval/v2/RHEL9/rhel-9.oval.xml.bz2' file which is referenced from datastream
Status: draft
Generated: 2024-02-26
Resolved: true
Profiles:
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high
Title: ANSSI-BP-028 (intermediary)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_intermediary
Title: ANSSI-BP-028 (minimal)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_minimal
Title: CCN Red Hat Enterprise Linux 9 - Advanced
Id: xccdf_org.ssgproject.content_profile_ccn_advanced
Title: CCN Red Hat Enterprise Linux 9 - Basic
Id: xccdf_org.ssgproject.content_profile_ccn_basic
Title: CCN Red Hat Enterprise Linux 9 - Intermediate
Id: xccdf_org.ssgproject.content_profile_ccn_intermediate
Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Server
Id: xccdf_org.ssgproject.content_profile_cis
Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Server
Id: xccdf_org.ssgproject.content_profile_cis_server_l1
Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l1
Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Workstation
Id: xccdf_org.ssgproject.content_profile_cis_workstation_l2
Title: DRAFT - Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171)
Id: xccdf_org.ssgproject.content_profile_cui
Title: Australian Cyber Security Centre (ACSC) Essential Eight
Id: xccdf_org.ssgproject.content_profile_e8
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Title: Australian Cyber Security Centre (ACSC) ISM Official
Id: xccdf_org.ssgproject.content_profile_ism_o
Title: Protection Profile for General Purpose Operating Systems
Id: xccdf_org.ssgproject.content_profile_ospp
Title: PCI-DSS v4.0 Control Baseline for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_pci-dss
Title: DISA STIG for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig
Title: DISA STIG with GUI for Red Hat Enterprise Linux 9
Id: xccdf_org.ssgproject.content_profile_stig_gui
Referenced check files:
ssg-rhel9-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-rhel9-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
security-data-oval-v2-RHEL9-rhel-9.oval.xml.bz2
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
Checks:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-oval.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-ocil.xml
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-cpe-oval.xml
Ref-Id: scap_org.open-scap_cref_security-data-oval-v2-RHEL9-rhel-9.oval.xml.bz2
Dictionaries:
Ref-Id: scap_org.open-scap_cref_ssg-rhel9-cpe-dictionary.xmlYou can any of the above Security Profile for your Rocky Linux server.
We have selected xccdf_org.ssgproject.content_profile_cis for demonstration in this Linux tutorial.
Running OpenSCAP Vulnerability Scan
Hopefully, You have selected the Security Policy and Security Profile by now.
Now, you can run an OpenSCAP Vulnerability Scan on your Rocky Linux server, by using oscap command.
# oscap xccdf eval \
--profile xccdf_org.ssgproject.content_profile_cis \
--results-arf arf.xml \
--report report.html \
/usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
WARNING: Datastream component 'scap_org.open-scap_cref_security-data-oval-v2-RHEL9-rhel-9.oval.xml.bz2' points out to the remote 'https://access.redhat.com/security/data/oval/v2/RHEL9/rhel-9.oval.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://access.redhat.com/security/data/oval/v2/RHEL9/rhel-9.oval.xml.bz2' file which is referenced from datastream
WARNING: Skipping ./security-data-oval-v2-RHEL9-rhel-9.oval.xml.bz2 file which is referenced from XCCDF content
--- Starting Evaluation ---
Title Install AIDE
Rule xccdf_org.ssgproject.content_rule_package_aide_installed
Ident CCE-90843-4
Result notapplicable
Title Build and Test AIDE Database
Rule xccdf_org.ssgproject.content_rule_aide_build_database
Ident CCE-83438-2
Result notapplicable
Title Configure AIDE to Verify the Audit Tools
Rule xccdf_org.ssgproject.content_rule_aide_check_audit_tools
Ident CCE-87757-1
Result notapplicable
Title Configure Periodic Execution of AIDE
Rule xccdf_org.ssgproject.content_rule_aide_periodic_cron_checking
Ident CCE-83437-4
Result notapplicable
Title Configure System Cryptography Policy
Rule xccdf_org.ssgproject.content_rule_configure_crypto_policy
Ident CCE-83450-7
Result notapplicableThe On-screen output of this command is quiet long, therefore, we are only show a couple of lines.
However, the results of OpenSCAP vulnerability scan were also stored in arf.xml and report.html files.
report.html file has better readability. You can open this file in a web browser.
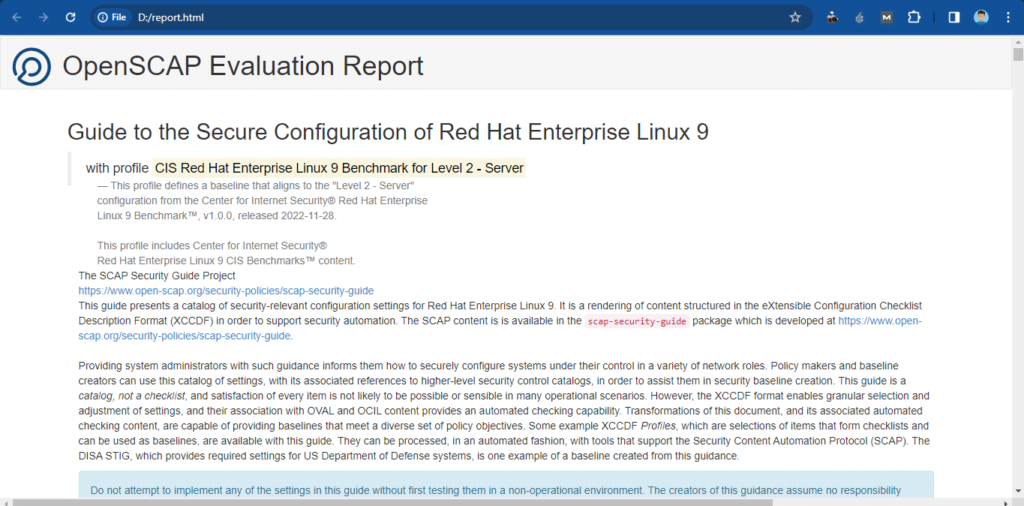
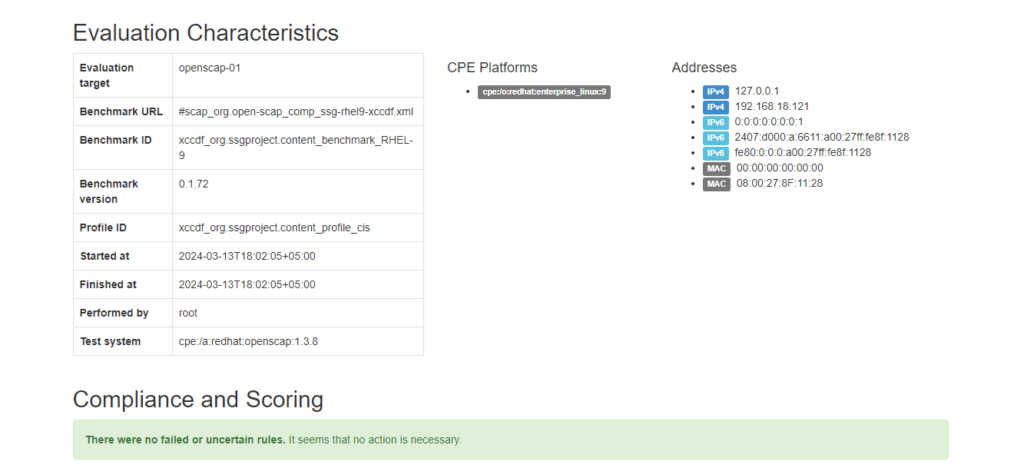
Frequently Asked Questions (FAQs)
1. How does OpenSCAP integrate with automation tools like Ansible and Puppet for compliance enforcement?
OpenSCAP can export scan results in machine-readable formats (ARF, XCCDF) and generate Ansible Playbooks or Puppet manifests for automated remediation. Tools like oscap-ansible and SCAP Workbench help bridge compliance checks with Infrastructure-as-Code (IaC).
2. How does OpenSCAP help with compliance?
OpenSCAP provides pre-defined security profiles (e.g., NIST, CIS, DISA STIG) and automated scanning to ensure systems meet regulatory requirements (e.g., HIPAA, PCI-DSS).
3. What operating systems support OpenSCAP?
OpenSCAP works on Linux (RHEL, CentOS, Fedora, Ubuntu, SUSE), Windows (partial support), and other Unix-like systems.
4. What are OpenSCAP’s main tools?
Key tools include:
– oscap (command-line scanner)
– SCAP Workbench (GUI tool)-oscap-docker (for container scanning)
5. Can OpenSCAP fix vulnerabilities automatically?
Yes, OpenSCAP can apply remediation using the --remediate flag in oscap, but manual review is recommended before applying changes.
Conclusion
In this tutorial, you have learned, how to install OpenSCAP tool on Rocky Linux 9 or other Red hat based Linux OS. We have also performed an OpenSCAP Vulnerability Scan on our Linux server.
Need expert AWS and Linux system administration? From cloud architecture to server optimization, I provide reliable and efficient solutions tailored to your needs. Hire me today!

Leave a Reply
You must be logged in to post a comment.